
Pioneering the Age of AI in Electronic Data Interchange (EDI) and Managed File Transfer (MFT)
End of Support Notification: IBM Sterling Data Exchange Select Products.
A data breach occurs when unauthorized individuals gain access to sensitive or confidential information, encompassing personal data like Social Security numbers and corporate data such as customer records or intellectual property. It’s important to note that not all cyberattacks are data breaches, and not all data breaches result from cyberattacks.
Data breaches specifically involve security incidents where data confidentiality is compromised. For example, a DDoS attack that overwhelms a website is not considered a data breach, but a ransomware attack that locks access to customer data and demands a ransom qualifies as one.
The Financial Impact of Data Breaches:
In 2022, organizations using AI and automation experienced data breaches that cost $3 million less on average compared to those without these tools. The global average cost of a data breach is approximately $4.35 million, while in the United States, it surges to an average of $9.44 million. A staggering 83% of surveyed organizations encountered more than one data breach.
Organizations across various sectors, including healthcare, finance, and the public sector, face significant consequences due to data breaches. The types of data handled in these sectors, such as government secrets, patient health information, and financial data, make the impact even more severe. For instance, the average cost of a healthcare data breach is $10.10 million, more than twice the overall average cost.
Data breach expenses comprise factors like lost business, revenue, and customers (averaging $1.42 million), the cost of detection and containment ($1.44 million), and post-breach expenses, including fines, settlements, legal fees, and reporting costs ($1.49 million).
Data Breach Reporting Requirements:
Data breach reporting can be complex and costly. Laws such as the U.S. Cyber Incident Reporting for Critical Infrastructure Act of 2022 (CIRCIA), HIPAA requirements for healthcare organizations, and state-specific data breach notification laws all demand prompt reporting and adherence to regulatory standards.
The General Data Protection Regulation (GDPR) also mandates swift notification to authorities in the event of a data breach when dealing with EU citizens, adding further layers of complexity and cost to data breach management.
Why Data Breaches Happen?
Data breaches can be the result of various factors, including innocent mistakes, malicious insiders, and hackers with diverse motives. Most malicious attacks are financially driven, with hackers seeking to steal credit card numbers, PII for identity theft, or data for sale on the dark web. However, some breaches aim to steal trade secrets, gather political information, or purely cause destruction.
Preventing and Mitigating Data Breaches:
Incorporating these controls and best practices can help organizations bolster their defences against data breaches and other cyber threats.
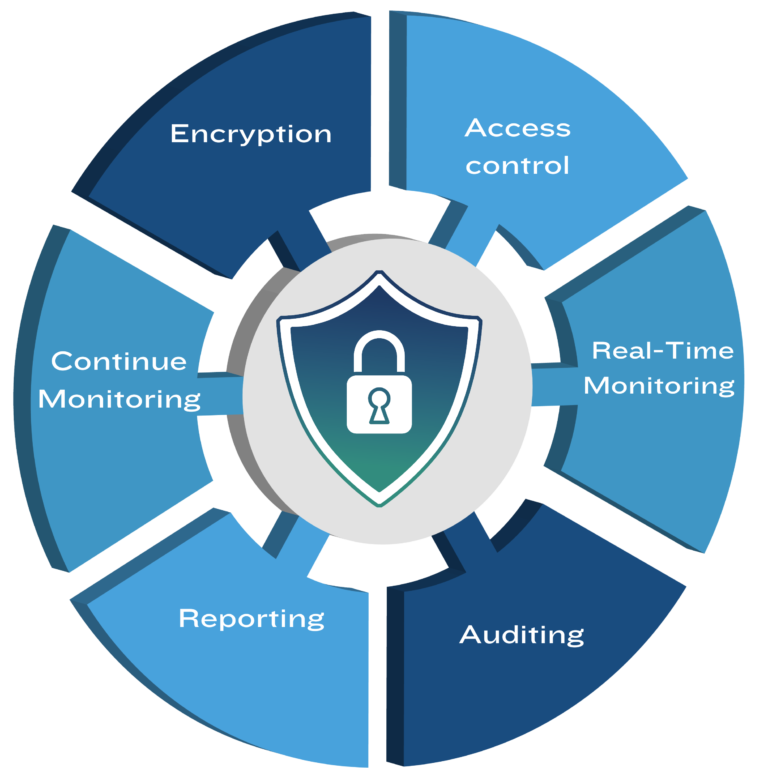
How Pragma Edge helps in securing your EDI or MFT gateways
We provide a range of effective tools and solutions to enhance data security and mitigate the risks associated with cyber threats.
IBM Partner Engagement Manager: Pragma Edge offers IBM Sterling Partner Engagement Manager, robust software for automating partner onboarding, assessing security, and generating compliance reports with advanced encryption & auditing.
Sterling Secure Proxy (SSP): Sterling Secure Proxy (SSP) is a security appliance that can be used to protect data from unauthorized access. It can do this by filtering traffic based on IP addresses, user IDs, and other criteria.
FileGPS: FileGPS is a File Monitoring Solution that helps you protect and track your sensitive files. This will help you to identify security threats and comply with data protection laws.
Jarvis Monitoring: Jarvis automates sterling processes with real-time monitoring, proactive alerts, and file tracking to ensure optimal performance and data protection compliance.
IBM Sterling Certified Containers: Scalability & Performance: Optimized for large organizations and built to scale. Easily handles increased demand without compromising on performance, suitable for businesses of all sizes.
Installing IBM Maximo APM - Asset Health Insights
What's new in IBM Maximo APM - Asset Health Insights 7.6.1
Browse Categories
Share Blog Post

Pioneering the Age of AI in Electronic Data Interchange (EDI) and Managed File Transfer (MFT)
End of Support Notification: IBM Sterling Data Exchange Select Products.

End of Support Notification: IBM Sterling Data Exchange Select Products.

Discontinuance of Support for IBM Sterling Data Exchange Select Products
End of Support Notification: IBM Sterling Data Exchange Select Products.
| Cookie | Duration | Description |
|---|---|---|
| cookielawinfo-checkbox-analytics | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Analytics". |
| cookielawinfo-checkbox-functional | 11 months | The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category "Functional". |
| cookielawinfo-checkbox-necessary | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Necessary". |
| cookielawinfo-checkbox-others | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Other. |
| cookielawinfo-checkbox-performance | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Performance". |
| viewed_cookie_policy | 11 months | The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. It does not store any personal data. |
Thank you for the Registration Request, Our team will confirm your request shortly.
Invite and share the event with your colleagues
Thank you for submitting your details.
For more information, Download the PDF.
To deliver next-generation B2B and File Transfer capabilities
IBM Partner Engagement Manager Standard is the right solution
addressing the following business challenges
IBM Partner Engagement Manager Standard is the right solution
addressing the following business challenges
IBM Partner Engagement Manager Standard is the right solution
addressing the following business challenges
Thank you for the Registration Request, Our team will confirm your request shortly.
Invite and share the event with your colleagues
